Buspirate v3.6 firmware upgrade from USB
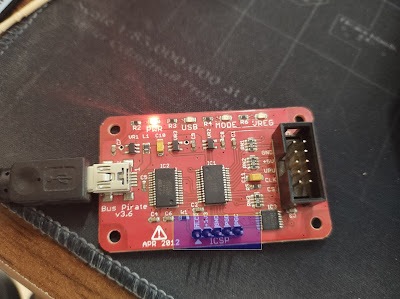
Buspirate: The Bus Pirate v3.6a, created by Ian Lesnet, is a troubleshooting tool that communicates between a PC and any embedded device over 1-wire, 2-wire, 3-wire, UART, I2C, SPI, and HD44780 LCD protocols - all at voltages from 0-5.5VDC. This product eliminates a ton of early prototyping effort when working with new or unknown chips. Upgrading Firmware: buspirate will not come with new firmware so it has to be change by us. buspirate v4 : Supports firmware version 7 buspirate v3.x: Supports firmware version 6&7 (note : firmware version 7 may hurt the device hardware not fully tested from my side doit in your won risk) Requirements: Buspirate firmware and loader : https://github.com/DangerousPrototypes/Bus_Pirate/tree/master/BPv3-bootloader ICSP pins. in these pins there are two of them which is PGD and PGC helps us to load the firmware into it . T he PGC and PGD pins with a jumper cable. When you are in the bootloader, the MODE LED of the Bus Pirate...

